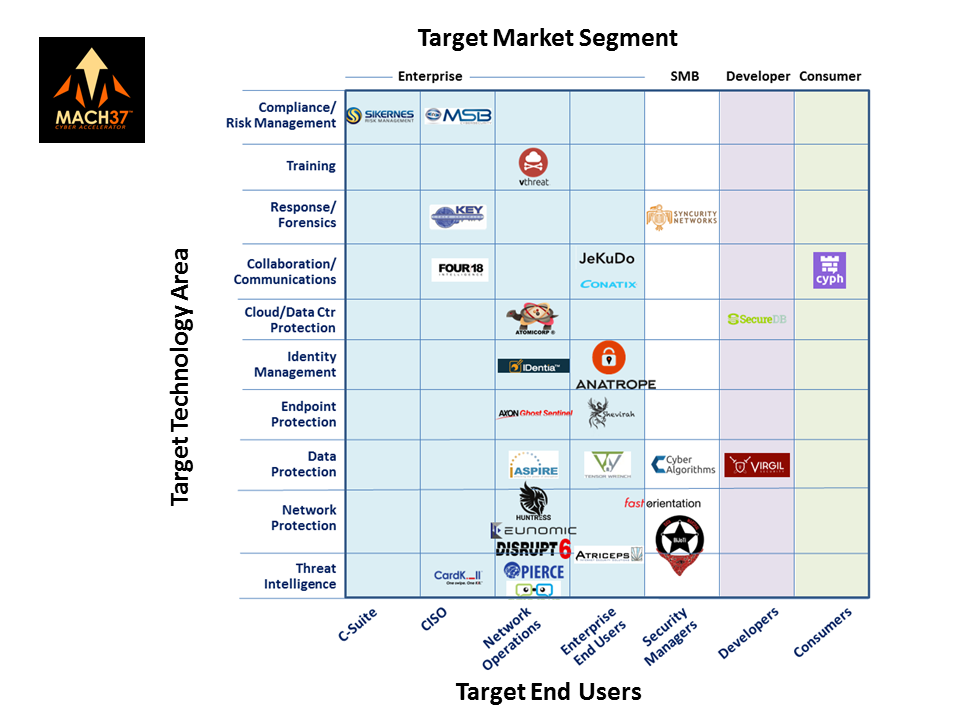
The cybersecurity market continues to evolve rapidly, with glimmerings of an emerging normalization as West Coast investors start to retreat from “frothy” valuations. We like to use the emerging capabilities of Mach37 as our window on the future (at much more attractive valuations than the West Coast), so that is the starting point. This is now the fifth cohort of Mach37 cybersecurity startup companies, bringing the total portfolio to 29 new companies. To help differentiate these companies for ourselves as well as potential investors we developed the following chart, showing both technology and market focus for these companies.
But as John Pescatore of SANS Institute pointed out at a Mach37 Security Leaders dinner earlier this fall, markets are probably more strongly defined by how people are structured to buy goods and services rather than how they are positioned to sell. This is where the market normalization seems to be taking place.
First, the large cloud providers are now fairly well established: AWS, Microsoft Azure, Google, Rackspace, Salesforce and a couple more. While some companies look to sell security capabilities for cloud implementations directly to end users (virtual firewalls, for example), it seems likely that these types of features will be increasingly offered directly by the cloud vendors rather than on a stand-alone basis.
Second, consolidation certainly continues among the more mature cybersecurity product companies, led by the FireEye acquisition of Mandiant but also in deals such as Intel’s acquisition of McAfee, Cisco’s acquisition of SourceFire in 2013, and ManTech’s acquisiton of Knowledge Consulting Group this year. In the threat intelligence portion of the market, the conventional wisdom is now that most threat intelligence feeds are very similar, with small incremental gains from aggregating two or more, making it more likely that every credible larger vendor will simply incorporate threat intelligence as part of their larger-scale service. Further, with the VC community raising less money for IT acquisitions and skepticism about the current high valuations, one could view these as signals that major portions of market consolidation have already taken place.
Third, as indicated in the recent Cyber Insurance blog post (see October 8), insurance companies and similar intermediaries are increasingly providing the access and funding streams for portions of the market such as forensics, pen testing, training, and remediation. Vendor offerings in these areas will likely need to work with these intermediaries as gatekeepers, since they will increasingly finance the response to incidents.
Fourth, hardware vendors in both mobile and business markets are increasingly incorporating information and cyber security in their basic package offerings. Dell for example is now including antimalware technology from Cyren to the Dell e-mail security appliances, and has just announced the deal to buy EMC. Samsung recently announced a partnership with WidePoint Corporation to add their identity management and access technologies to Samsung Galaxy phones. In September, Microsoft purchased Israeli cloud security company Adallon to improve Microsoft’s core offering. And the list goes on.
Certainly there are still wide-open market niches for a variety of technologies, and greatly under-served portions of the market, including small businesses. But as the apparent market normalization continues, cybersecurity startups will need to sharpen their focus and value proposition, or else develop some truly disruptive capabilities rather than simply the buzzword-level disruptions we often see.
Where might these disruptions come from? One look at the headlines shows that privacy, cryptowars, and identity management are hot button issues. The transition to IPv6 will open a variety of new opportunities as people begin to understand the implications of that change. Resiliency in the face of system compromise is an emerging issue, specifically the ability to continue operating without leaking information even though devices or networks are compromised or under attack. The Internet of Things and its future impact on society are enormously misunderstood and under-appreciated.
We are still a long way from secure, networked computing, but the current set of technologies and product offerings seems to be maturing rapidly. Anyone looking to start a company or enter this market needs to have their antennae finely tuned to the market signals they receive.
Dave: Good work. We need to get the latest cohorts on the graph.